Intel is currently investigating the leakage of private keys associated with the Intel Boot Guard security feature after the recent cyberattack on Micro-Star International (MSI) by the Money Message extortion gang. The leaked private keys could potentially compromise the ability of the Boot Guard feature to prevent the installation of malicious UEFI firmware on MSI devices.
The Boot Guard private keys were reportedly generated by MSI for use with Intel’s Boot Guard technology, which is designed to meet Windows UEFI Secure Boot requirements. Intel Boot Guard provides a hardware-based root of trust for firmware image verification, preventing the loading of unauthorized firmware, or UEFI bootkits, that could hide their activities from the kernel and security software, persist through operating system reinstalls, and facilitate malware installation on compromised devices.
The leaked private keys affect 116 MSI products, according to Alex Matrosov, CEO of firmware supply chain security platform Binarly. Matrosov warns that the leak could render Intel Boot Guard ineffective on MSI devices using 11th Tiger Lake, 12th Adler Lake, and 13th Raptor Lake CPUs. The leaked keys enable attackers to craft malicious firmware updates that can bypass Intel Boot Guard’s verification, using the normal BIOS update process with MSI update tools.
With the leaked private keys, attackers can sign their malware to bypass Boot Guard, rendering the security feature useless on affected MSI devices. Since Boot Guard’s security is baked in at the silicon level with fuses in the chips, there is no straightforward fix to revoke the leaked keys or generate and use new private-public key pairs for existing machines. This places MSI-based computer systems currently in use at risk of being targeted by adversaries using the leaked private keys to sign code that passes verification checks.
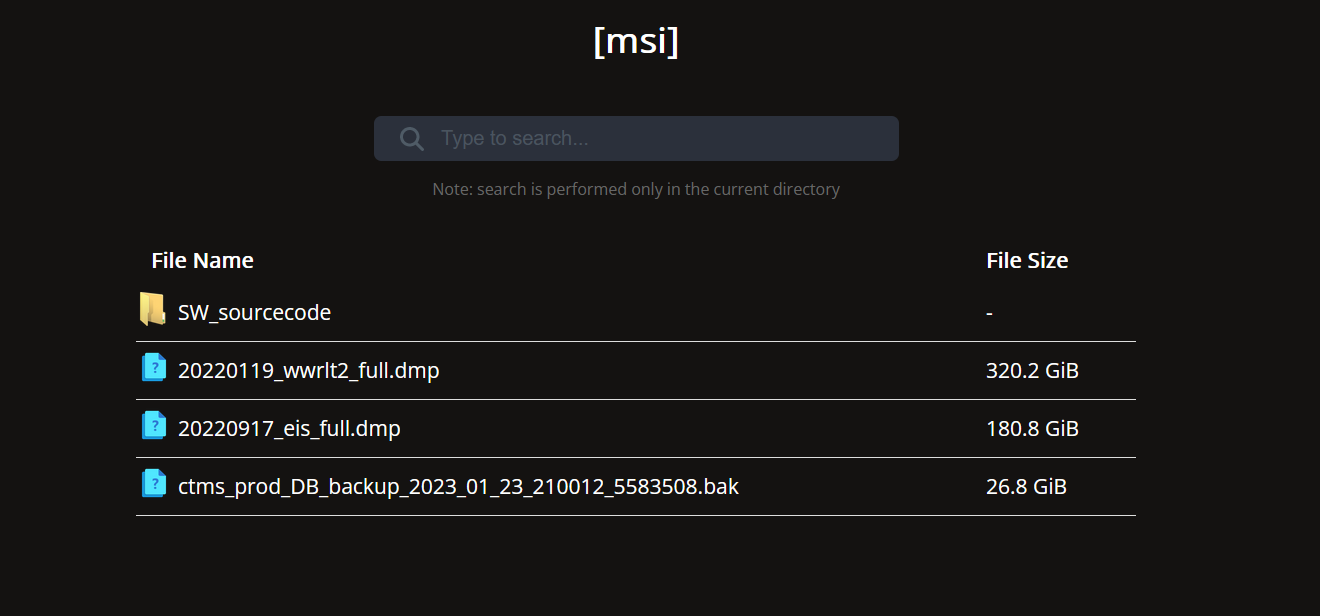
The data breach occurred in March when the Money Message extortion gang attacked MSI, claiming to have stolen 1.5TB of data, including firmware source code, private keys, and BIOS firmware. The attackers demanded a $4 million ransom and subsequently leaked some of the stolen data on their leak site after not receiving payment.